The access control system is installed for the purpose of preventing loss and preventing crime, so it must have high reliability. An access control system may not have an alarm during most of its operation, so there is no need for an alarm. The probability of an alarm requiring an alarm is generally small, but if the alarm system fails within this minimum probability, It often means the arrival of disaster. Therefore, the access control system must implement reliability design and reliability management at all stages of design, installation and use to ensure high reliability of products and systems.
In addition, in the system design, equipment selection, commissioning, installation and other aspects are strictly implemented the national or industry-related standards, as well as the relevant departments on the safety technology prevention requirements, the product must undergo a number of authoritative certification, and has many typical The user has been running normally for many years. Security access control and security systems are used to protect people and property, so the system itself must be safe. The high security mentioned here also refers to the natural or quasi-natural attributes of the product or system, and should ensure the safety of the equipment, the operation of the system and the safety of the operator.
device installation
1, front-end equipment
2, the central control room equipment
Equipment commissioning
1. After the system is installed, first access the signal of the access control card reader to the host, and then separately detect the situation of the access control card reader, whether there is any false negative or false alarm. After the road detection is no problem, it is connected to another road. In this way, each road is tested separately, and all the lines are connected after the confirmation is correct.
2. The management personnel can separately authorize according to the authority of the user. For example, some personnel can enter and exit any place at any time. The ordinary personnel can only enter and leave the authorization scope within the authorization time by the authorization card. When all access points are normally turned on and turned on illegally, check if the control center computer has a record.
3. If the central computer cannot be connected to the controller due to malfunction or other reasons, can the controller independently record the relevant information of the controlled door point. When the central computer is connected, can all information be automatically uploaded, and whether the information record can be guaranteed intact? Sex.
4, do a good job of debugging records.
5. Finally fill in the completion report.
Pipeline installation
1. The installation engineering wiring shall comply with the national regulations “Construction and Acceptance Specifications for Electrical Installations†and relevant national regulations and regulations. Threading in the pipe or in the trunking shall be carried out after the construction plastering and ground works.
The water and debris in the pipe or in the trunk should be removed before threading. Lines of different systems, different voltage levels, and different current types should not be worn in the same tube or in the same slot of the slot. The wire shall be inside the pipe or in the trunking and shall not have joints or kinks.
The connectors of the wires shall be soldered in the junction box or connected by terminals. Small-section system connections can be spliced, the number of twisted turns should be more than five inches, then tinned, wrapped with insulating tape. When the pipeline passes through the deformation joint of the building, compensation measures shall be taken. The conductors shall be fixed across the deformation joints with sufficient margin. Terminals in the terminal box should be crimped or terminal strips with solder joints, and the terminals should have a label.
2. The access controller should be installed firmly, not tilted, and should have obvious signs. Installed on a lightweight partition wall, reinforcement measures should be taken. Introduce the cable or wire of the access controller, the wiring should be neat and avoid crossover, and the part of the cable core wire and the wire to be fixed should be fixed, and the drawing should not be faded; the terminal block and each terminal, wiring No more than two; the cable core and the wire should be left with a margin of not less than 20cm; the wire should be bundled into bundles; after the wire lead-through wire is threaded, it should be sealed at the inlet pipe.
3. The main power inlet of the access controller should be directly connected to the power supply. It is strictly forbidden to use the power plug. The main power supply should have obvious signs; the grounding of the access controller is firm and has obvious signs.
4. The routing and specifications of the monitoring indoor grounding busbar should meet the design requirements.
The following rules should be met during construction: the surface of the grounding busbar should be complete, no obvious damage and residual flux slag, copper busbar light, slippery burr, no cracking of the insulation layer; grounding busbar should be placed in the ground trough or cable The center of the walkway is fixed on the outside of the frame slot. The busbar should be flat and must not be skewed or bent.
The connection between the busbar and the rack or the roof should be firm; the copper busbar on the cable walkway can be fixed by screws, and the copper stranded busbar on the cable walkway should be tied to the crossbar; the system lightning protection grounding installation should be Construction in strict accordance with design requirements. Grounding installation should be carried out simultaneously with civil construction.
Basic functions realized by a mature access control system: management of access rights to channels
1. Permission to enter and exit the channel: that is, for each channel, which people can enter and exit, and who can not enter or exit;
2, the way to enter and exit the channel: is to authorize the entry and exit mode of the person who can enter and exit the channel;
3, access control system: access mode usually has password, card reading (biometric), card reading (biometric) + password three ways;
4. The time period of entering and leaving the channel: it is to set the time when the person who can use the channel can enter and exit;
5, real-time monitoring function: system management personnel can view the entry and exit of each door area personnel (with photo display) and the status of each door area (including door switch, various abnormal status alarms, etc.) in real time through the microcomputer; It is also possible to open or close all door areas in an emergency;
6, access record query function: the system can store all the entry and exit records, status records, can be queried according to different query conditions, equipped with corresponding attendance software can achieve attendance, access control card;
7. Abnormal alarm function: Under abnormal conditions, it can realize microcomputer alarm or alarm alarm, such as: illegal intrusion, door timeout not closed, etc.
According to the different access control systems of the system, the following special functions can also be realized.
Anti-submarine back function: the cardholder must enter and exit according to the pre-set route, otherwise the next channel card is invalid. This feature is to prevent cardholders from following others.
Anti-tailing function: the card holder must close the door that has just entered to open the next door. This function is the same as the anti-submarine back implementation, but in a different way.
Fire alarm monitoring linkage function: In the event of a fire alarm, the access control system can automatically open all electronic locks to allow people inside to escape. Linkage with monitoring usually means that the monitoring system automatically records the current situation when someone swipes the card (valid/invalid), and also records the situation when the access control system has an alarm.
Network settings management monitoring function: Most access control systems can only be managed by one computer, while advanced technology systems can set up monitoring and query management of the entire system at any authorized location on the network, or can be set up remotely through the Internet. Manage monitoring queries.
Multi-card door opening function: Simply put, the same door requires several people to swipe the card at the same time (or other way) to open the electric control door lock! Implement the logic to open the door.
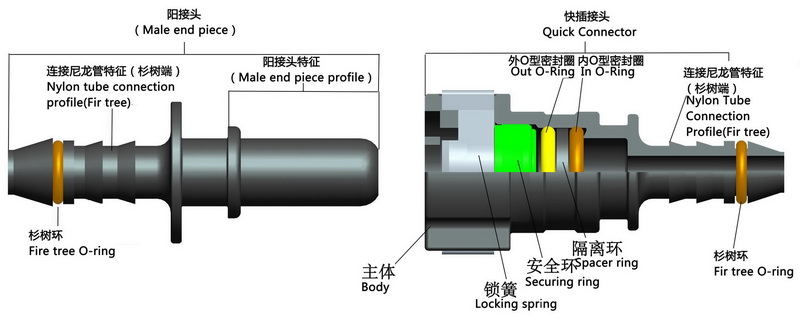
Shinyfly Quick Connector is composed of body, in O-ring, spacer ring, out O-ring, securing ring and locking spring. When inserting another pipe adapter(Male End Piece) into the connector, since the locking spring has certain elasticity, the two connectors can be connected together with the buckle fastener, and then pull back to ensure the installation in place. In this way, the quick connector will work. During maintenance and disassembly, first push in male end piece, then press locking spring end till expansion from the middle, the connector can be easily pulled out. Lubricated with SAE 30 heavy oil before re-connecting.
Shinyfly Quick Connectors are designed and produced strictly in accordance with the SAE J2044-2009 standards (Quick Connect Coupling Specification for Liquid Fuel and Vapor/Emission Systems).
Innovative, secure, "quickfit" - Shinyfly quick connect fittings are made of synthetic materials and suitable for most media fluid transmission systems. Whether it's fuel, cooling water, oil vapor or urea SCR systems, we can always provide you with efficient and reliable connections as well as the best solution.



Quick Connector
Nylon Quick Connector, Platic Quick Connector, Nylon Tube Connector, Assembly Fasterner, Quick Disconnect
Linhai Shinyfly Auto Parts Co.,Ltd. , https://www.chinashinyfly.com



